In an age where everyone downloads videos, music, or memes daily, media files have become an unexpected weapon for cybercriminals. What seems like an innocent image or video could actually be a trap — delivering malware into your system without your knowledge.
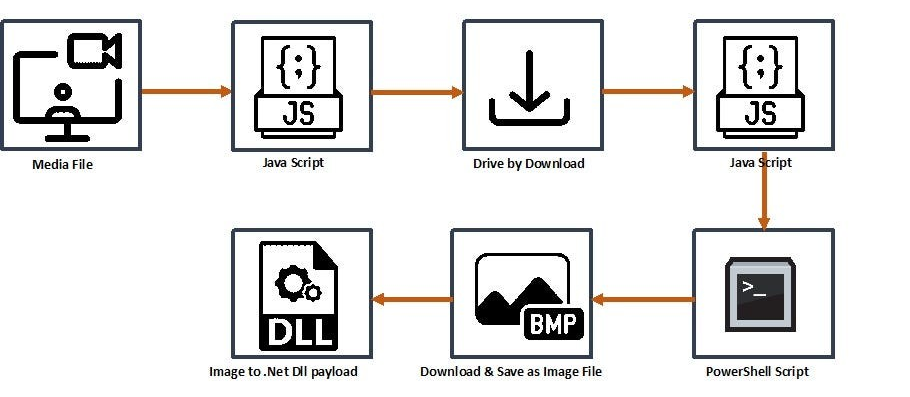
Let’s break down how this attack works, step-by-step, based on a common malware delivery chain:
In the underground world of cybercrime, one of the most effective tricks hackers use is luring users with adult content. Many users, especially on untrusted or shady websites, try to download free porn videos — only to end up downloading malware that infects their system.
🧪 Breakdown of the Attack Chain:
When the JavaScript file is opened in Sublime Text, part of the code appears obfuscated. However, before reaching that section, the script executes command-line instructions in hidden mode.
Copy the obfuscated line of code, then open Microsoft Edge’s Developer Tools by pressing F12. In the console tab, type allow pasting and press Enter. After that, paste the copied code into the console for execution or analysis.
After running the JavaScript code in the Edge browser console, it reveals a few important details. First, it shows the word 'GET', which means the script is trying to fetch data from the internet. Then it shows a URL: http://paste.ee/d/sR3qd83V/0, which is likely a link to the next part of the malware. The script is using this link to download more harmful code. It also shows 'MSXML2.ServerXMLHTTP.6.0', which is a method used by Windows to make internet requests silently in the background. This means the malware can talk to a remote server, download more files, and run them without the user knowing. All of this shows that the media file and script are working together to infect the system step by step.
Download the file from http://paste.ee/d/sR3qd83V/0 , “this.toString().replace(/\/\*(\[(?:[^\[]+)?\[)((?:[\r\n]|.)*?)\]\]\*\//gi, f);” suggests the script is using embedded resource unpacking, a technique used to hide malicious payloads within JavaScript comments and retrieve them at runtime.
This script is a heavily obfuscated JavaScript malware loader designed to evade detection and deliver a hidden payload. It builds long strings using unreadable characters.
The obfuscated script was pasted into the Edge browser’s Developer Console, where it was decoded and executed. This process revealed the hidden PowerShell command embedded within the script. The decoded output shows how the malware uses in-memory execution to evade detection and run silently.
The headstrongly variable contained an obfuscated Base64 string, which was decoded using CyberChef. Upon decoding, it revealed a PowerShell command that fetches a malicious image file (wp4096799-lost-in-space-wallpapers.jpg) hosted on an external domain. This file is downloaded using WebClient, likely hiding malware, and executed in memory to evade detection and bypass security policies.
While analyzing the malware, the original link to download the image was no longer active, so the same image file (ss.png) was added manually from the local disk. The modified script reads this local image, scans for a hidden BMP signature, and extracts pixel-level RGB data to reconstruct an embedded payload. This payload is then Base64-decoded and saved as payload.bin, which is actually a DLL file likely meant for malicious execution.
IOC:
Sample:32D6C54BCDF901E48323CDB2D203E8A9
JS:9E5FD82FE9B8652EE14B29D6C2E254ED
Drivebydownload:CB0C04ADAE3C71F12DAD255D24EFEC21
ImageFile:653b229acfce50f27cd65039840861ec832b0c74f9b82f6bc96084b54337928e
“Updated Code to Save File without Executing https://drive.google.com/file/d/1rsj0810C6ezVP5R7ZKRPOHdQE2MRDHxO/view?usp=sharing “
Learn more 🔞 The Hidden Danger Behind Downloading Porn Videos: A Malware Trap in Disguise