Research Paper By Rohan Verma
Abstract
This paper addresses the psychological motivations behind game players’ decisions to download third-party video game algorithms, with focus on the tension between legitimate modding and illegitimate hacking. Integrating well-established theoretical Frame works such as the Technology Acceptance Model (TAM), Theory of Planned Behavior (TPB), risk benefit analysis, and moral disengagement, the research examines the extent to which views about usefulness, social norms, perceived behavioral control, and cognitive justification affects the gamers’ actions. The analysis emphasizes how blurred lines between creative extension and exploitative hacking and community standards elide definitions of legitimacy. Psychological drivers such as character identity through game avatars, emotional immersion, reward-loss evaluation, and rationalization of morality are determined to play primary roles in adoption choices. Through consolidation of these perspectives, the paper argues that gamers’ choices cannot be considered technical or opportunistic, but are deeply rooted in social, moral, and cognitive processes. This analysis gives a more nuanced appreciation of digital behaviors, shedding light on motivations behind both creative engagement and rule-breaking practices within online gaming cultures.
Literature Review
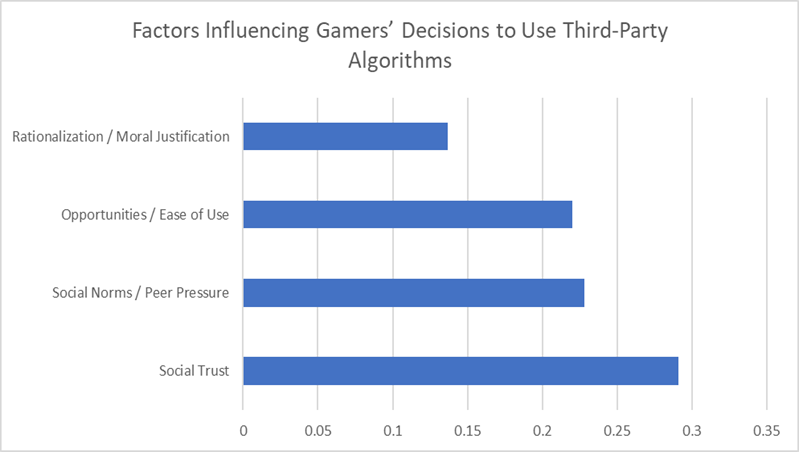
Gamer acceptance behavior on third-party algorithms has been examined through different theoretical lenses, highlighting various aspects of psychology, sociality, and behaviors. Researchers distinguish legitimate modding community-initiated creative changes that enhance aesthetics or expand material and illegitimate hacking, which exploits game mechanics in unfair manners (Consalvo, 2007). Modding is viewed by most as participatory culture (Postigo, 2007), adding value to the gaming community, while hacking is decried as undermining fairness and violating rules (Kow & Nardi, 2010). The boundary, however, at times is blurred. “Gray areas” emerge wherein quality-of-life hacks (i.e., auto-loot, UI improvement) are considered innocent by gamers or unauthorized by creators (Taylor, 2018). These conflicts point to the tensions between community norms, developer policies, and gamer justifications in perceptions of legitimacy. Risk-benefit analysis gives us a peek into the cost-benefit decisions made by gamers prior to embracing unauthorized algorithms. Studies on computer decisions (Slovic, 2000) indicate that people trade off potential enhancement of their performances, prestige, and time saving against risks involved in detection, account ban, or reputational loss. Younger and competitive gamers tend to be most likely to take risks in search of reward (Király et al., 2014).
Moral disengagement, as theorized by Bandura (1999), is essential in understanding why certain gamers rationalize illegal actions. Euphemistic labeling (“it’s merely a tool”), shifting of responsibility (“everyone does it”), and diffusion of responsibility (“my team does it”) alleviate guilt. Moral disengagement is associated with cheating in both educational and game settings, as research shows (Detert et al., 2008; Chen & Wu, 2015). In game environments, unhappiness with pay-to-win systems or perceptions of unfairness typically fortify rationalizations in employing hacks (Consalvo, 2009).
Player-game interactions also influence adoption decisions on third-party tools. Characters in games, avatars, and game personas influence emotional engagement, social interactions, and moral decisions (Turkay & Kinzer, 2014). Experiments indicate that alignment with morally “justified” roles decreases guilt and negative emotions, and playing in unjustified roles augments moral conflict (Hartmann & Vorderer, 2010). Therefore, character affiliation and moral identity impact whether or not players find third-party changes as creative freedom or as unethical exploitation.
Source: Abacademies (2021), PubMed (2021)
INTRODUCTION
There is an emerging market in which data analytics firms sell companies pricing algorithms that enable companies to price more profitably. Some third-party developers would tend to have a superior pricing algorithm than would be developed internally by a company due to having more knowledge and experience, access to greater data, and greater incentives to invest in their development (since the pricing algorithm can be licensed by numerous companies). Treating a pricing algorithm as merely another input, companies could well achieve efficiencies by outsourcing that input. Meanwhile, antitrust authorities themselves have been concerned that in arriving at the “make or buy,” anticompetitive impact arises since it results in rivals implementing a pricing algorithm by the same third party. Additionally, there exists a bit of evidence, and allegations of evidence, that anticompetitive impacts have arisen. Plaintiffs in apartment rentals and hotels markets in the United States allege implementation by a third party’s pricing algorithm yielded supracompetitive prices.
The level of this efficiency provided by the third party is a function of the level of demand variability. When a firm adopts the pricing algorithm, it pays a fee to the third party (fixed by the third party as a function that maximizes its own profit) and bears a firm-specific adoption cost. Equilibrium adoption is demonstrated as increasing in the level of demand variability and, in addition, there exists a critical threshold such that there is widespread or nearly widespread adoption of the pricing algorithm if and only if there is greater than that threshold level of demand variability. Although diffuse adoption by competitors of a third party’s pricing algorithm can underscore concerns over potential anticompetitive mischief, it is demonstrated by this study that the procompetitive efficiency is most robust in the case of diffuse adoption. Therefore, antitrust enforcers need to be careful before limiting a third party in a marketplace in which there is widespread adoption by firms of its pricing algorithm.
Even now, the chances of a successful career in competitive esports are low among casual gamers. Like with classical sports, playing at a professional level requires absolute dedication and commitment by players, who train 70–80 hours a week in order to be the absolute best in their game. The teams/players usually live together in order to make most of the time they have for training, hone in on team strategy, tactics, and communications, and hone individual abilities by playing every day against other brilliant players. Intricate systems develop around the players in order to keep them in shape for important matches. Training agendas involve creating new tactics, honing existing ones, and sparring against other teams and players in order to test abilities and find weaknesses. Even though they are playing video games, there are numerous occasions in which physical and mental well-being are essential in achieving a successful outcome, and therefore most teams integrate nutrition, physical training, and psychological support in their everyday activities.
Although the audience for esports is smaller for now than that of major traditional games like football, it has a different advantage — tremendous potential for growth. Right now, only ~15% of the gaming audience watches esports as well. But as more games lay a solid foundation, that percentage will increase. An estimated 3 billion people worldwide are gamers today, ~500 million watch esports, which means there is currently 2.5 billion untapped potential. That gives us more than favorable soil on which to establish the necessary momentum to expand the gamer audience in the coming few years.
The difference between “legitimate modding” and “cheating” is community-based, creative tweaking that adds or enhances a video game without disturbing its competitive equilibrium. These tweaks are generally designed to enhance the player’s enjoyment through graphical enhancements, cosmetic alterations, or new content in the form of new quests, maps, or storylines. Developers usually allow or encourage legitimate modding by releasing official modding platforms or tools like Steam Workshop. In gaming communities, legitimate modding is usually encouraged as a type of participatory culture and creative expression, and it adds depth and longevity to a game.
On another hand, illegal hacks use unauthorized third-party algorithms or software, created with no goal but to exploit game mechanics in a method that gives undue advantage. Some are bots in first-person shooters, wall-hacks, which disclose unseen enemies, or auto-resource collection bots. Unlike creative mods, hacks are unfair, tilting matches, and breaking intended rules of engagement. Developers, in their End-User License Agreements, do not allow the practices and actively impose penalties, including bans, among exploiters. Even if there are some certain subcultures among gamers that rationalize hacking, the larger community and industry as a whole declare it as a form of cheating, in spite of its detrimental effect both on gameplay integrity and on the gaming ecosystem itself.
While in principle the line between legitimate modding and illegal hacking is clear, in practice the line is often blurry, generating a gray area in gaming culture. Quality-of-life mods, for example, like auto-loot functions, inventory managers, or improvement in interface with the game world could be viewed as innocent by gamers, yet a few game developers regard them as unauthorized changes since they manipulate gameplay pacing. Cosmetic mods in general are innocent, yet if such mods unlock paid cosmetics or skip microtransactions, they cross into exploit territory by disrupting a game’s business model. Competitive situations generate yet another gray area: a visual improvement mod that enhances the ability to perceive game elements could be ignored in solo modes but be viewed as unfair in ranked matches. Perception by groups in the community further causes confusion, since what a certain club views as an innocent adjustment, another club views as cheating.
In addition to this, there are circumstances in which gamers tend to defend the use of hacks by citing grievances in game design, for example, oppressive monetization, and thus a culture of moral disengagement is fostered. These nuances indicate that legitimacy cannot be solely by the technical nature of the mod, yet by social conventions in the game community, by the nature of competition, and by developer policy. Consequently, the demarcation between creative contribution and unfair exploitation is fluid and ever-changing and mirrors the dynamic nature of digital gameplay and relationships with game developers.
Source : Pew Research Center (2008), Time2Play (2022), AT&T/CBR (2021)
Psychology of technology adoption
1) Technology acceptance model (TAM)
The main goal of TAM was to illuminate processes underlying technology acceptance, with a goal of predicting the behaviour and giving a theoretical account of the successful application of technology. The practical goal of TAM was notifying practitioners on actions that they could take before systems implementation. With the established link between technology acceptance in organisations and firms’ productivity, the investigation on technology acceptance stayed as a focus in the research agenda following the creation of the original TAM. Even though the broad application of TAM verified the strength of the theory (it explained on average approximately 40% of the variance in technology acceptance), the model’s creators intended on enhancing its predictability yet again.
The reason why the extension was needed was a low understanding of the conditions underlying the perception by users on technology utilisation. The suggested extension, by the label TAM2, consisted of five new exogenous variables and two moderators. The newcomers and moderators added in TAM2 were: subjective norm, image, job relevance, output quality, result demonstrability, experience and voluntariness. Subjective norm is “a person’s perception that most people who are important to him think he should or should not perform the behaviour in question”. This variable was considered as impacting intention directly as well as indirectly through the medium of image and perceived usefulness.
TAM and its extensions have been applied in numerous applications in various fields, situations and geographical areas, providing a valuable theoretical tool as far as user behaviour is concerned in terms of prediction. In addition to the application in the field of information systems management, technology acceptance models have been employed in other fields e.g. advertising and marketing. Since information systems are drastically utilised in product and service marketing, TAM proved a useful tool in examining the consumer attitude towards technological innovations, such as online shopping tools, e-commerce websites and chatbots, facilitating online trade.
TAM, for instance, was applied in examining the perception of online shopping tools by customers, underlying their purchase intention through online e-commerce websites. Indeed, it was verified that in addition to trust, TAM constructs account for a significant amount of variance in the attitude towards IS tools and the following consumer behaviour. Furthermore, TAM was effective in facilitating the explanation concerning the acceptance of online e-commerce chatbots, which accounted for purchase intention (Araújo & Casais, 2020). Nevertheless, in both situations whereby the model was applied in potential and repeated customers in online store coverage, the model itself was capable of predicting only the behaviour of the customers who already possessed earlier exposures concerning the coverage by the online stores.
2) Theory of Planned Behavior (TPB)
TPB traces out the causal connections from beliefs through to actual human behaviour and it is suggested that individuals make decisions through rational consideration of information that is available. Behavioural beliefs, normative beliefs, and control beliefs are three types of consideration to direct behaviour. Behavioural beliefs are theorised as “the likely consequences or other attributes of the behaviour”. Behavioural beliefs are attitude determinants, whereby attitude is a learned tendency and it represents a person’s evaluation of a desired behaviour’s desirability. From a deductive perspective, the greater the positive attitude, the greater a person’s intention will be to engage in the behaviour.
These three beliefs are presumed to be easily accessible in a person’s memory and respectively lead to attitude towards the behaviour, subjective norm, and perception of behaviour control, which in combination predict behavioural intention. TPB remedied the shortcomings of TRA by the addition of control beliefs and the perceived behaviour control construct in a case in which people intend to act but do not have control or means necessary to perform behaviour. This was significant as it enhances the power of a theory in everyday world situations in which a person’s capability or external pressures and constraints operate in determining whether or not a person can actually engage in a specific behaviour.
They found that males were more inclined to be influenced by their referents and the effect of perceived behavioural control was greater for older populations. Regarding personality traits, Hsu et al. (2017) investigated the moderation role of price sensitivity in influencing people’s purchase intention of green skincare products. They found that the effects of attitude, subjective norm, and perceived behavioural control were stronger for people with higher price sensitivity. Intention is held to be the most influential determinant of behaviour in TPB. It indicates an individual’s readiness or how much effort they are willing to exert to perform the targeted behaviour. A positive relationship is expected between intention and behaviour.
Source: Time2Play (2022), Irdeto (2018), PlaySafe ID / Atomik Research (2025)
3) Moral Disengagement
Moral disengagement is a collection of eight cognitive processes that inactivate the self-sanctions that usually force us to act morally (Bandura, 1990, 1999). The application of these processes decreases the dissonance people feel as they participate in morally questionable actions and allow their participation without usually accompanying negative cognition or emotions. Individuals can be either actively or passively involved in moral disengagement.
For instance, if circumstances allow disadvantageous social comparisons, persons can actively utilize rationales for irresponsible behaviors. When a person interprets employee theft as merely a way to rebalance equity or as a corrective measure against employers’ failure in meeting their responsibility, then theft appears nearly the ethical thing to do. Once socialized in morally disengaged cognitions like “my employer owes me this,” persons can comfortably glide into a host of unsavory actions ranging through dishonesty, theft, and cheating, social undermining and sexual harassment believing somehow they are justified in undertaking them. Moral disengagement thereby functions as a moral compass, shifting the compass needle in favor of an activity that can be morally defended by its processes.
Some of these processes may fit perfectly with different categories of our taxonomy (e.g., reframing one’s action may be part of the judgment of correct moral behavior). However, we see these processes as functioning primarily through reducing the importance of morality to the circumstance or in one’s actions. For example, euphemistic labeling functions primarily by using words that remove one’s action from moral relevance. In the same way, dehumanization may promote perceptions that the victim is not worthy of moral concern. Evidently, moral disengagement is a complex phenomenon that involves an interplay of behavioral, personal, and environmental factors, stemming from the social cognitive theory of moral agency from which it is part (Bandura, 1986).
Although an extensive number of studies have been conducted in this area, reviews to date have primarily focused on the role of moral disengagement in enabling bullying. Notably, there has been little synthesis of the literature that investigates links between moral disengagement and other forms of aggressive and antisocial behavior, and also the potential factors that may moderate its enlistment. It is therefore important to establish the extent to which these variables are associated with moral disengagement as a proxy to minimizing occurrence of transgressive conduct.
Psychological Factors
The game character, which establishes the role that a person takes on in a video game, is the main tool by which a player’s interaction with the virtual world is established. Game characters are integral to the game and are capable of influencing a player’s actions. Players are influenced by the external attributes of the game character and also by the character’s implicit characteristics, both capable of impacting the degree of a player’s personal engagement and their identity in the game. As the video game market continues to develop at a quickening pace, the visual description of the game scene grows ever more subtle and game characters all the more lifelike. Consequently, players are capable of getting a closer understanding and feeling for the game characters on whom they are playing and the game in general.
Studies have found that the features of the game characters in violent video games (such as appearance, race, costume, and moral attributes) have an effect on the players. The more attractive the appearance of the game characters, the more confident the players are in the social context; as a result, the players have closer relationships with other players in the game, which shapes stronger interactions. The players in black garments display a stronger tendency toward aggression in virtual tasks and weaken group cohesion. Individuals playing Black characters tend to have more negative assessments and exhibit more aggressive behavior after playing a game. Research has also shown that characters from different countries can have an effect on individuals. A study by, in which the research subjects were required to play characters acting against their country in an educational electronic game, found that this could promote attitude changes to a certain degree.
There are many impactful elements in game characters: not only external aspects including clothes and faces, but also significant attributes including identity and morality. The most significant attribute in game characters is morality. Many researchers have explored the issue by giving game characters different types of in-game missions, e.g., attacking foreign territories for justified or unjustified reasons. The results showed that, if a player played a “good” game character in a violent game (e.g., Righteous Army or Counter-Strike), negative emotional experience and moral panic triggered by playing games was less. Studies also showed that empathy decreased aggression in the justified-role, yet increased it in the unjustified-role. Also, in the unjustified-role, there were still more worries, hurts, and negative emotional experiences among the players. Studies also showed that negative emotions and moral anxiety are less if people played the justified roles in, e.g., Ally of Justice and Counter-Strike.
Conclusion
This paper illustrates how perceptions of perceived usefulness and social approval (TAM), attitudes and normative pressure (TPB), cost–benefit ratios (risk–reward profiles), and mechanisms of moral disengagement all converge in why game players justify and react to the decision in the broader adoption of third-party tools. The distinction thus established also between honest modding and dishonest hacking in turn illustrates the complex cultural trade-offs in the gaming cultures, where boundaries of honest creativity and exploitation are constantly being redrawn. Further, the effect of game characters and player identity highlights the ways in which immersion and role-play morality can shape perceptions of acceptable behavior. Individuals who identify with justified or prosocial roles feel less moral restraint, but audiences in roles perceived by themselves to be unjustified are disposed towards more use of rationalizations in justification of exploitative behavior. Collectively, these results highlight that downloading third-party algorithms is not an isolated behavioral choice but the result of interwoven psychological, social, and cultural processes. For policymakers, developers, and community leaders, an understanding of these processes comes a long way towards healthier gaming environments. Encouraging legitimate modding and addressing the root causes forcing players toward hacks like unfairness, monetization issues, or social pressures can counterbalance innovation, creativity, and equity inside online spaces.
References
· https://www.sciencedirect.com/science/article/abs/pii/S0165176524004956
· https://www.bcg.com/publications/2023/how-esports-will-become-future-of-entertainment
· https://open.ncl.ac.uk/theories/1/technology-acceptance-model/
· https://open.ncl.ac.uk/theories/18/theory-of-planned-behaviour/
· https://legal.thomsonreuters.com/blog/risk-benefit-analysis-deciding-on-risk-vs-reward/
·https://www.frontiersin.org/journals/psychology/articles/10.3389/fpsyg.2017.01863/full
· https://www.sciencedirect.com/topics/psychology/moral-disengagement